Ransomware is one of the most disruptive and prevalent types of malware in use today. This article provides an introduction to ransomware, and the dangers associated with extortion software. We explain what this malware is and how it works, examine the current ransomware landscape, and offer advice on how best to counter this cyber threat.
Ransomware Definition
Ransomware is an ever-evolving malware that blocks access to files or devices until the victim pays a ransom. The majority of ransomware uses encryption to render data unusable. Attackers then demand money for the decryption keys. If the victim ignores the demand, the attacker deletes the key and, as a result, makes all encrypted data useless.Ransomware can infect a single PC or a mobile device, but an attack can also go after an entire network. Ransomware can have devastating consequences. It can lead to:
- Loss of business and customer data.
- Legal repercussions for allowing a data breach.
- Prolonged downtime.
- A reputation hit that leads to a loss of customers.
- A costly recovery process that takes weeks to restore the network back into a pre-attack state.
- Long-term damage on infrastructure.
- Ransomware The consequences of ransomware can be crushing and lead to:
- Loss of business and customer data.
- Legal repercussions for allowing a data breach.
- Prolonged downtime.
- A reputation hit that leads to a loss of customers.
- A costly recovery process that takes weeks to restore the network to a pre-attack state.
- Long-term damage to infrastructure.
- Ransom requests range from a few hundred dollars to millions. Most attackers demand payment in Bitcoins, a choice of currency that allows the criminal to remain anonymous after receiving the money.
- Hackers use ransomware to target SMBs, enterprises, public organizations, and individual users. This malware can also be a threat to Windows, Linux and Mac. No business or system is safe, so ransomware prevention must be a part of every cybersecurity strategy.
- The Current State of RansomwareRansomware continues to evolve as criminals work on new tactics for exploiting the advances in cloud computing, virtualization, and edge computing. Below are the most notable trends currently shaping the ransomware landscape:
- Pressure on MSPs: Criminals are targeting managed service providers (MSPs) more than ever before. Breaching a single MSP creates an opportunity to infect clients and allows an attacker to go after multiple targets with a single breach.
- Better defenses: Companies are trying to stay ahead of hackers with new tactics. Improved heuristics, behavior analysis, and bait files are helping companies predict attacks instead of responding to dangers.
- Targeting work-from-home companies: Hackers are continuing to go after teams that operate remotely. The main target is employees who use personal devices to work remotely. Healthcare and education facilities are most vulnerable as criminals know their data is valuable and likely poorly protected.
- More RaaS than ever: Ransomware-as-a-Service is a subscription-based “service” that allows hackers to use third-party tools to carry out attacks. Tool creators get a percentage of each successful breach, while “clients” get to focus entirely on spreading malware.Biggest threats: The most prominent ransomware in 2021 are Conti, Avvadon, REvil (ex Sodinokibi), Netwalker, and Babuk.
The most common attack vectors remain phishing emails, RDP exploits, and software weaknesses.
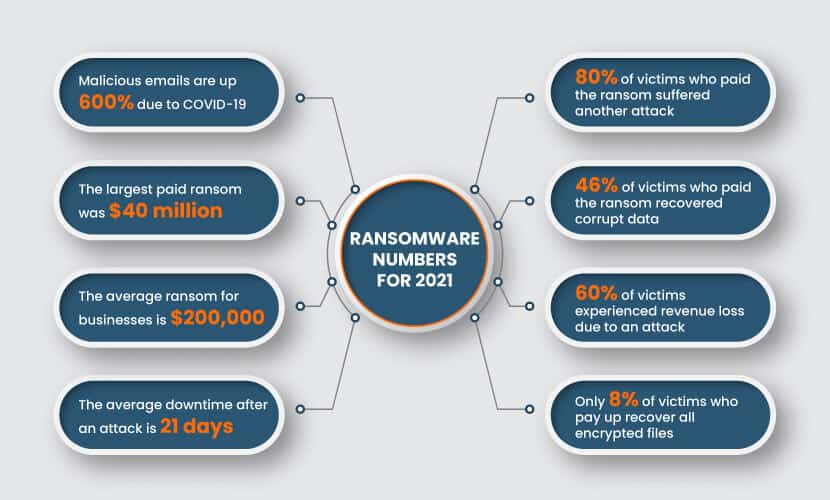
Our article about ransomware statistics presents eye-opening facts that demonstrate the danger behind this cyber threat.
How Does Ransomware Work?
- All ransomware attacks start with an initial infection when a malicious payload enters the system. The ransomware then executes the malicious binary once it is inside the system. Depending on the type of malware, the goal of the payload is to:
- Automatically search for target data (Microsoft Word documents, images, databases, etc.) and starts encryption.
- Connect to the hacker’s C&C server and grant direct control over the system.
- Automatically lock the operating system and device.
- Search for valuable data and set up the exfiltration process.
- Once the program completes its task, the user loses access to files or the entire computer. The device will display a message explaining the ransomware attack and the only way to restore control or recover data is by paying a ransom. The two common ways programs display this message are:
- A background that changes to a ransom note.
- Text files within each encrypted directory
Typically, every ransom has two deadlines to put pressure on the victim. First, the hacker will double the ransom. The second deadline is the date when they plan to delete the key. This type of cryptography uses two unique keys to encrypt or decrypt data. Most ransomware programs use a different decryption key for each target file. Most ransomware programs use a different decryption key for each target file.
A cyber kill chain allows a security team to define each step in a ransomware attack and use it as an opportunity to detect and stop the threat.
How Does Ransomware Spread?
Here are the most common methods criminals use to spread ransomware:
- Email phishing campaigns that spread a corrupt link or attachment.
- A highly targeted spear-phishing attack.
- Different forms of social engineering (baiting, scareware, pretexting, tricks on social media, etc. ).
- Malvertising.
- Exploit kits on malicious websites.
- A custom worm that exploits a system weakness (such as a faulty RDP setup or a flaw due to poor server management).
- An infected piece of hardware (namely USBs and laptops).
- Unwanted add-ons during downloads.
- Most top-tier ransomware can spread via the network after infecting the initial victim. In some cases, the device infected is not the target of the attack but rather an endpoint. Typical targets are databases and servers, so most programs use self-propagating mechanisms to spread to other systems.
Who Does Ransomware Target?

Ransomware criminals attack anyone they can, but their primary targets are companies that seem willing to pay a hefty ransom quickly. Most attacks go after victims that:
Keep valuable client data (for example, banks or law firms).
- Require immediate access to files (hospitals and clinics).
- Have irreplaceable data (government agencies).
- Rely on an understaffed security team (public institutions and SMBs).
- Have a disparate user base and a lot of file sharing (universities).
- Do not feel safe if your business does not fall under these criteria. Criminals will take advantage of any opportunity to target vulnerable people. Also, some ransomware spreads automatically across the Internet, so every company is a potential target regardless of size, industry, or income level.
How Many Types of Ransomware Are There?
While all ransomware programs follow a similar blueprint, there are two main types of these cyberattacks:
Locker ransomware (computer locker):
- A type of malware that locks users out of their device and prevents the computer from booting up. Typically, the locked system allows limited access so that the victim can interact with the hacker.
Crypto ransomware (data locker):
An attack that encrypts valuable data without locking the user out of the device. The most common targets include financial data, personal information, large projects, photos, tax information, videos, etc.Locker Ransomware is less dangerous as it does not corrupt files or move across networks. It is easier to remove this malware without paying the ransom. This is why locker hackers will often pose as police officers in order to force the victim to pay the ransom. A Doxware attack looks to exfiltrate data from the target system. Some programs will first steal data before encrypting files. A mix of crypto and Doxware capabilities allows an attacker to use both extortion tactics.
Our article about different ransomware examples provides an in-depth look at the world’s most notorious extortion programs.
How to Avoid Ransomware?
Ransomware can be hard to stop, but a combination of employee awareness, proactive response planning, and basic security hygiene can help. Below are the best practices every business should implement to protect against ransomware:
Keep devices and systems up to date with the latest security patches.
Ensure the team uses strong email security practices.
Organize security awareness training to ensure the team knows how ransomware works.
- Use network segmentation to prevent lateral movement between systems.
- Ensure employees know how to use anti-malware and virus solutions.
- Emphasize the importance of safe surfing to avoid malicious ads and drive-by downloads.
- Improve overall network security.
- Rely on zero-trust policies and multi-factor authentication to protect vital systems and databases.
- Monitor network activity for suspicious behavior.
- Ensure endpoints do not become an entry point with regular updates and traffic monitoring.
- Create an incident response plan.
- The best way to minimize the threat of ransomware is to use immutable backups. Immutable backups are uneditable so that intruders can’t encrypt, remove, or alter information. Back up data multiple times per day to minimize the risk of losing data if ransomware strikes.
- Our article about ransomware prevention presents 18 security practices and measures that help keep this cyber threat at bay.
What to Do in Case of a Ransomware?
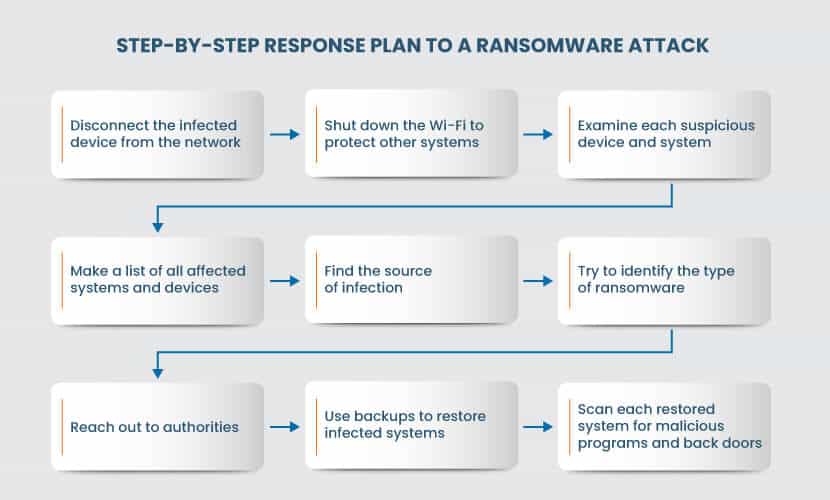
Even the best ransomware protection is sometimes not enough to prevent an attack. If you suffer an attack, follow the steps below to minimize the damage and quickly return to business as usual:
Isolate the problem.
Take the infected device offline and shut down the network. The program is likely looking for other devices and drives, so remove the possibility of lateral movement.
Assess the damage.
- Examine each suspicious device. Examine each suspicious device. Look for files with unusual extensions and encrypted data. Also, check for reports that users are having problems opening files. Find patient zero. You need to identify the source of attack. Look for alerts from your anti-virus and malware programs, EDR system, and monitoring platform.
- Identify the ransomware. You need to determine the type of ransomware that attacked your company. You can identify the person who sent the ransom note by typing the text of the message into a search engine. You can restore the device to its last known safe state if you have an immutable backup. If you don’t have a backup, and the police doesn’t possess the key to decrypt the data, then your only option is to pay the ransom. Consider the following before making a decision:
- There is a chance you will never receive the decryption key.Many victims have paid the ransom only to get nothing in return.
- The decryption key may not work.The ransomware creators are not in the file recovery business, so criminals do not spend much time ensuring the decryption works.
- Your files may be too corrupted. However, consider the following before making the decision:
- There is a chance you never get the decryption key. Many victims have paid the ransom only to receive nothing in return.
- The decryption key may not work.
Ransomware creators are not in the file recovery business, so criminals do not spend much time ensuring the decryption works.
Your files may be too corrupted.
- Some ransomware programs corrupt files beyond repair to ensure encryption happens as quickly as possible. Even if you have a decryption code, it may not be enough to restore your files. The same team may strike again in the future or let their colleagues know about what companies are willing to meet the demands.Criminals can still leak your data.
- If attackers exfiltrate your data, nothing can stop them from selling the data to the highest bidder even if you pay the ransom.Instead of weighing whether paying the ransom is the right move or not, ensure your company can handle a ransomware attack. You will never have to pay the ransom if you take the right precautions and make backups. This article will help you educate your team on the dangers of ransomware and how to prevent it. In our guide, you can also learn about the differences between Malware and Ransomware.
