In this article you will learn:
- Why every organization needs a cybersecurity incident response policy for business continuity.
- The Seven critical security incident response steps (in a checklist) to mitigate data loss.
- What should be included in the planning process to ensure business operations are not interrupted?
- Identify which incidents require attention & When to initiate your response.
- How to use threat intelligence to avoid future incidents.
What if your company’s network was hacked today? What if your company’s network was hacked today? It is more than likely that you will experience a cybersecurity event in 2023. Cybercriminals constantly develop new strategies for breaching systems. Preparation for these events can reduce the damage and loss you and your stakeholders. Preparation for these events can decrease the damage and loss you and your stakeholder’s.
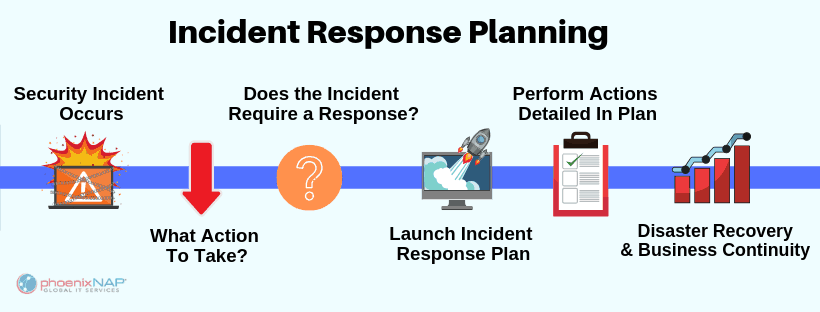
Having a clear, specific, and current cybersecurity incident response plan is no longer optional.Cyber incident plan flow chart
What is an Incident Response Plan?
An incident response (IR) plan is the guide for how your organization will react in the event of a security breach.
Incident response is a well-planned approach to addressing and managing reaction after a cyber attack or network security breach. The goal is to minimize damage, reduce disaster recovery time, and mitigate breach-related expenses.
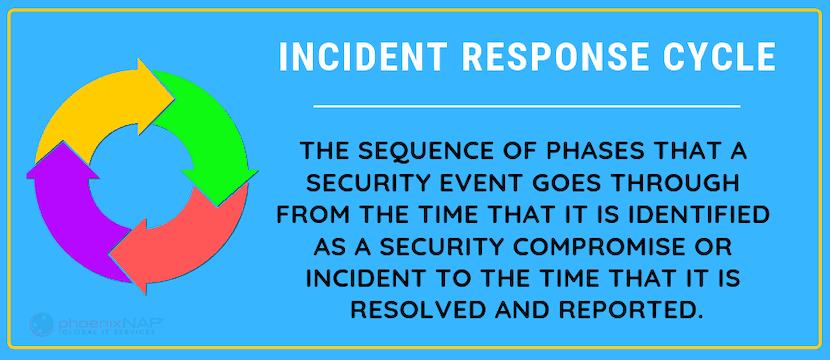
Definition of the Incident response life cycle.
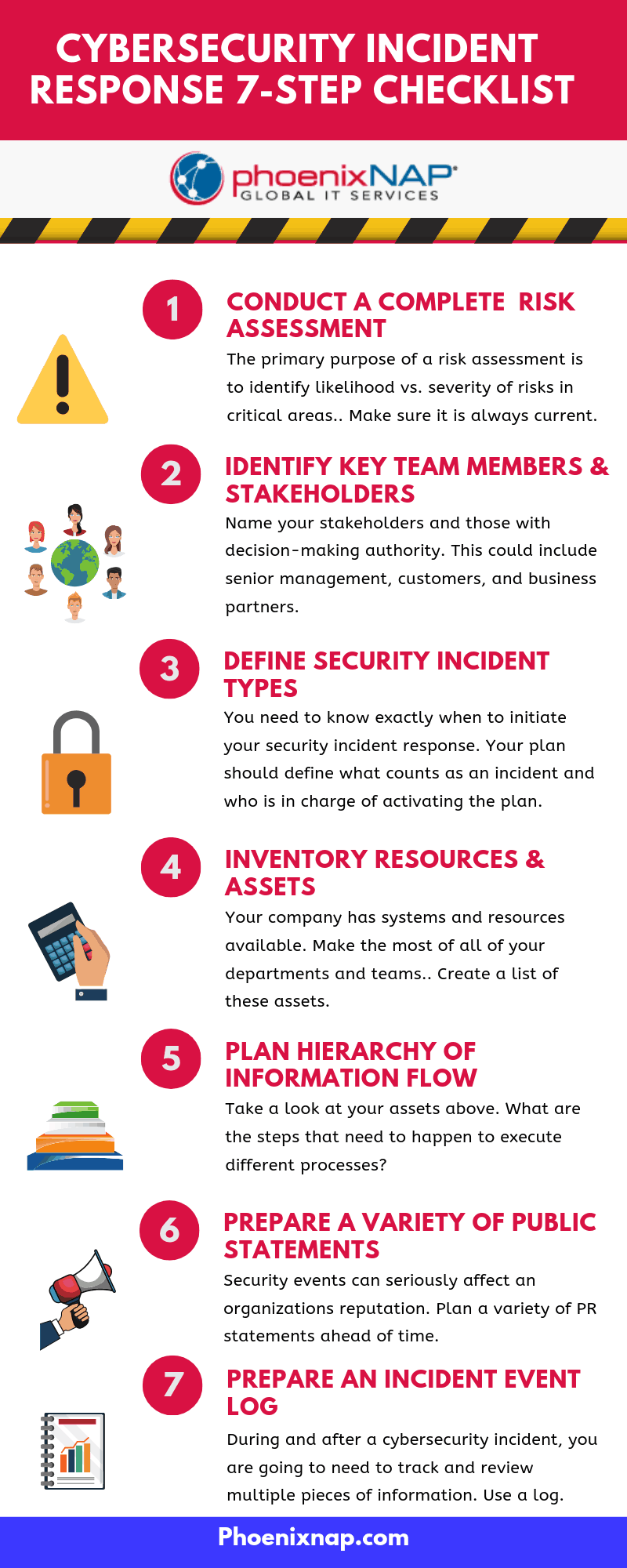
Cybersecurity Incident Response Checklist, in 7 Steps
During a breach, your team won’t have time to interpret a lengthy or tedious action plan.Keep it simple; keep it specific.
Checklists are a great way to capture the information you need while staying compact, manageable, and distributable. Checklists are a great way to capture the information you need while remaining compact, manageable, and distributable.
1. Focus Response Activities with a Risk Assessment
If your organization has not conducted a risk assessment for a possible incident, it is time to do so. Any risk assessment should be primarily focused on identifying the likelihood and severity of potential risks in key areas. It’s important to make sure that any cybersecurity risk assessment you have done is up-to-date and relevant for your current systems. If It’s out-of-date, perform another evaluation.
Examples of a high-severity risk are a security breach of a privileged account with access to sensitive data. It is particularly important if there are many users affected. Your IR plan should include specific contingency plans if this risk is likely to occur. Use the Department of Homeland Security’s risk assessment tool to prioritize and identify severe risks. Plan for low and medium-risk items, too. This will allow you to avoid focusing your efforts on the worst-case scenarios. Remember that even a breach of “medium risk” could be devastating.
2. Identify Key Team Members and Stakeholders
Identify key individuals in your plan now, both internal and external to your CSIRT. Name the decision makers and stakeholders. This could include senior management, customers, and business partners.
Document the roles and responsibilities of each key person or group. They should be trained to perform the functions. Store multiple contact details online and off. Plan to have a variety of contact methods available (don’t rely exclusively on email) in case of system interruptions. Cyber Incident Scoring System
3. Define Incident Types and Thresholds
You need to know exactly when to initiate your IT security incident response. Your response plan should define what counts as an incident and who is in charge of activating the plan.
Know the kinds of cybersecurity attacks that can occur — stay-up-to-date on the latest trends and new types of data breaches that are happening.
Defining potential security incidents can save critical time in the early stages of breach detection. The stronger your CSIRT’s working knowledge of incident types and what they look like, the faster you can invoke a targeted active response.
Educate those outside your CSIRT, including stakeholders. These stakeholders should be aware of these thresholds and incident definitions. Establish a clear communication plan to share information amongst your CSIRT and other key individuals to convey this information.
4. Inventory your resources and assets.
IR response relies on coordinated action between many departments and groups. You have different systems and resources available, so make the most of all of your departments and cyber incident response teams.
Create a list of these assets, which can include:
Business Resources:
Team members, security operations center departments, and business partners are all businesses resources. These should consist of your legal team, IT, HR, a security partner, or the local authorities.
Process Resources:
A key consideration is to evaluate the processes you can activate depending on the type and severity of a security breach. Include in your IR Plan resources such as partial containment, “watch-and-wait” strategies and system shutdowns, like deactivating web pages. You can reduce the impact of affected systems by managing security risks. Recovery Plan Hierarchies & Information Flow
Look at the assets you have listed above.
What steps are required to implement different processes? Who is your incident response manager? Who is the contact for your security partner?
- Design a flowchart of authority to define how to get from Point A to Point B. Who is in charge of shutting down your website on a short-term basis? What steps need to happen to get there?Flowcharts are an excellent resource for planning the flow of information. NIST provides some useful tools that explain
- precisely at a moments notice. This type of communication map is subject to frequent changes. After a major departmental restructure, or any other transition, make special plans to update the flowcharts. This may require you to go beyond your normal review process.6. Prepare Public Statements
Security events can seriously affect an organizations reputation. Public perception is key to reducing the negative effects of these breaches. How you interface with the public about a potential incident matters.
Describe how (and with whom) you are solving the problem and what corrective action has been taken.
Explain that you will publish updates on the root cause as soon as possible. how to disseminate information Use caution when talking about actual numbers or totalities such as “the issue is completely resolved.”
Be consistent in your messaging
Be open to conversations after the incident in formats like Q&A’s or blog posts
Plan a variety of PR statements ahead of time. Be consistent in your messaging. best practices recognized by the IAPP include Be open to conversations after the incident, such as Q&A’s or blog posts.
- Plan a variety of PR statements ahead of time. It may be necessary to contact media outlets. If you have to inform the public about a security breach, it is important that you prepare a statement template. When preparing your PR statements, it is important to consider this question. For these statements, timing is key – balance fact-checking and accuracy against timeliness.
- Your customers are going to want answers fast, but don’t let that rush you into publishing incorrect info. Your reputation will be damaged if you publish incorrect information about the number of clients affected or what type of data was compromised. It is better to publish data you are confident about rather than later clean up the mess caused by a false statement. Prepare an incident event log.
- During a cyber-attack, you will need to review and track multiple pieces of data. How, when and where was the breach discovered and how did it get addressed? Prepare a template in advance to make it easier to complete. Prepare a template ahead of time, so it is easy to complete.
- This log should include:
- Location, time, and nature of the incident discovery
- Communications details (who, what, and when)
Any relevant data from your security reporting software and event logs
After an information security incident, this log will be critical. It is impossible to conduct a thorough incident review without an event log. This log will be used by security analysts to evaluate the effectiveness of your response, and any lessons learned. This account will also support your legal team and law enforcement both during and after threat detection.
How Often Should You Review Your Incident Response Procedures?
To review the steps in your cybersecurity incident response checklist, you need to test it. Run potential scenarios based on your initial risk assessment and updated security policy.
Perhaps you are in a multi-user environment prone to phishing attacks. If you’re a major target of a DDoS, your testing agenda may look very different. It is recommended that you conductannual tests.
- But your business may need to conduct these exercises more frequently.
- Planning Starts Now For Effective Cyber Security Incident Response
- If you don’t have a Computer Security Incident Response Team (CSIRT) yet, it’s time to make one. The CSIRT is the main driver of your cybersecurity incident response plans. Critical players should include members of your executive team, human resources, legal, public relations, and IT.
Your plan should be a clear, actionable document that your team can tackle in a variety of scenarios, whether it’s a small containment event or a full-scale front-facing site interruption.
Protecting your organization from cybersecurity attacks is a shared process. Partnering with the experts in today’s security landscape can make all the difference between a controlled response and tragic loss. Partnering with experts in today’s security landscape can make the difference between a controlled response and a tragic loss.