Insider threats are increasing in all industries. Threats can come from anyone with access to sensitive data.
Be prepared to mitigate your risk with active insider threat detection and prevention.
- What is an Insider Threat?
- Insider threats are defined as cybersecurity threats that come from within your own company. Insider threats can be anyone who has valid access to your network. This includes employees, vendors and even former employees. Anyone that has valid access to your network can be an insider threat.
- Dealing with insider threats isn’t easy since the people you trust with your data and systems are the ones responsible for them.
Types of Insider Threats
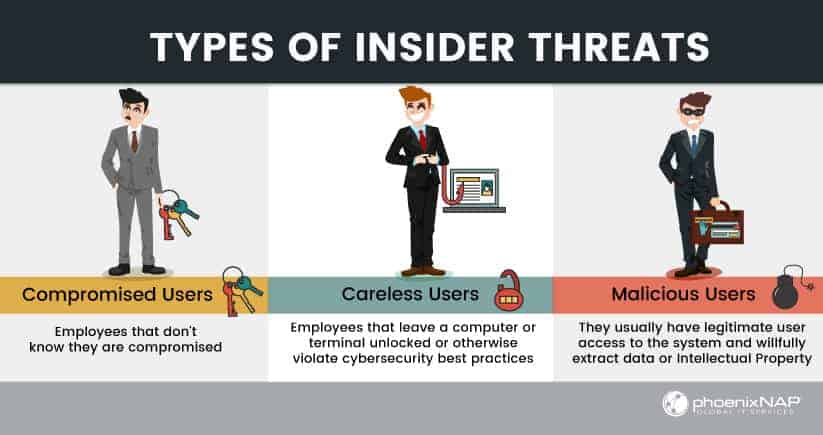
There are three types of insider threats, Compromised users, Careless users, and Malicious users.
Compromised Employees or Vendors
Compromised employees or vendors are the most important type of insider threat you’ll face. Insider threats are most likely to come from compromised employees or vendors. This can happen when an employee clicks on a link from an email that is phishing. These are the most common types of insider threats.
Careless Employees
Careless employees or vendors can become targets for attackers. Leaving a computer or terminal unlocked for a few minutes can be enough for one to gain access.
Granting DBA permissions to regular users (or worse, using software system accounts) to do IT work are also examples of careless insider threats.
Malicious Insider
Malicious attackers can take any shape or form. Malicious Insider
Malicious attackers can take any form. They can also hide their tracks since they are part of the attack. That makes detection even more difficult.
Detecting Insider Threats
Most of the security tools used today try to stop legitimate users being compromised. These include firewalls, anti-phishing software, and endpoint scanners. It’s not surprising that they are the most common breaches. It’s almost impossible to determine whether a system event is valid when it comes from careless behavior. Network and security admins probably don’t know the context behind an application’s behavior, so won’t notice anything suspicious before it’s too late.
Similarly, with malicious attackers, they will know the ins and outs of your company’s security system. The most important issues in detecting insider threat are:
1. Legitimate Users
The threat’s nature makes it difficult to stop. The actor is using their real login profile, so there is no immediate alert. Accessing large files or databases infrequently may be a valid part of their day to day job requirements.
2. Context of System and Software
The security team needs to be able to recognize bad behavior in order to detect it. It’s not easy to do. Business units are usually the experts in their own software. Without the right context, detecting a real insider threat from the security operations center is almost impossible.
3. Post Login Activities
Keeping track of every user’s activities after they’ve logged in to the system is a lot of work. In some cases raw logs must be checked and each event examined. This can be a huge amount of work, even with Machine Learning tools. It could also lead to many false positives being reported, adding noise to the problem.
Indicators of Insider Attacks
Detecting attacks is still possible. Some signs are easy to spot and take action on.
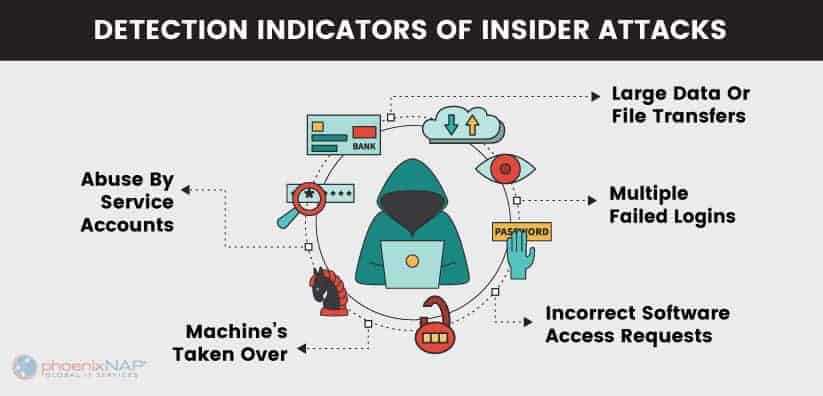
Common indicators of insider threats are:
Unexplained Financial Gain
Abuse by Service Accounts.
Multiple failed logins.
Incorrect software access requests.
- Large data or file transfers.
- Using systems and tools that look for these items can help raise the alarm for an attack. While regular endpoint scans (daily) will ensure workstations stay clean from viruses and malware.
- Identifying Breaches in the System
- Identify breaches starts with the security team understanding normal behavior.
- Normal behavior should be mapped down to the lowest access and activity. Included in the logs should be the User’s ID, workstation IP address, the accessed server’s IP, employee department, and the software used.
Additionally, knowing what database was accessed, which schemas and tables read, and what other SQL operations were performed, will help the security team identify breaches.
Detect Insider Threats with Machine Learning
One area where machine learning gives a massive ROI is in network threat detection. It’s not magic, but it can help you identify suspicious and weird actions. By providing the state of your system and behavioral data to a machine-learning algorithm, strange and suspicious actions can be quickly identified. Information like user and connection types, role access and application rights, working times and access patterns, can promptly be passed to ML applications.
Knowing what falls outside of the above normal system state can be done by mapping the following into the alert process:
Listing table access rights per app.
Specifying service account credentials and schemas used.
Monitoring the usual data storage locations.
Prevent Insider Threats With Threat Scoring
Correlating the above types of information allows you to create threat scores for each user activity. This type of analytics has never been used before in the industry. Early implementations have been successful in helping companies gain the edge on their rivals.
- Vendors are starting to offer custom Security Risk Management solutions that include:
- Behavior analytics
- Threat intelligence
Anomaly detection
Predictive alerts
Statistics on Insider Threats
33% of organizations have faced an insider threat incident. Source: SANS
- Two thirds of insider incidents are caused by employee or contractor negligence. (Source: Ponemon Institute)
- 69% of organizations have experienced an attempted or successful threat or corruption of data in the last 12 months. It takes on average 72 days to contain a threat from an insider. You can identify high-risk profiles by mapping their daily interactions with data that you manage. This will allow you to proactively engage in the areas where you have the biggest concerns.
- Although any point in the network poses a risk, elevated access rights have the highest potential for abuse. Implementing key indicator monitoring on these user profiles with active directory policies will reduce the amount of risk you face.
- Auditing exiting employees, ensuring their credentials are revoked and they do not leave with company data is also vital. Nearly
70% outgoing employees admit taking data with them to the door
. You may as well open the door for them if credentials are left intact. Privileged access management is a great way to manage user.
Although unintended insider threats remain the biggest concern, it’s the malicious ones that can cause the worst disaster.