RaaS is an illegal spin on as-a-service business models (e.g., SaaS or PaaS), which allows less tech-savvy This article will explain everything you need to know about Ransomware As A Service, including what it is, how to use it, and why criminals We also present the most effective ways to protect yourself against RaaS-style attacks.
Worried about ransomware?
You are not alone – in the year 2022, 71% out of all businesses were targeted by an attack. Keep your data safe with pNAP’s ransomware protection services and our unique mix of immutable backups and cloud-based disaster recovery.
What Is Ransomware as a Service (RaaS)?
Ransomware as a Service (RaaS) is a pay-for-use “business model” that enables criminals to rent pre-developed malware to carry out ransomware attacks. RaaS benefits both criminal parties:RaaS operators (authors of ransomware) take less personal risk, scale attacks, and receive a percentage of each paid ransom.
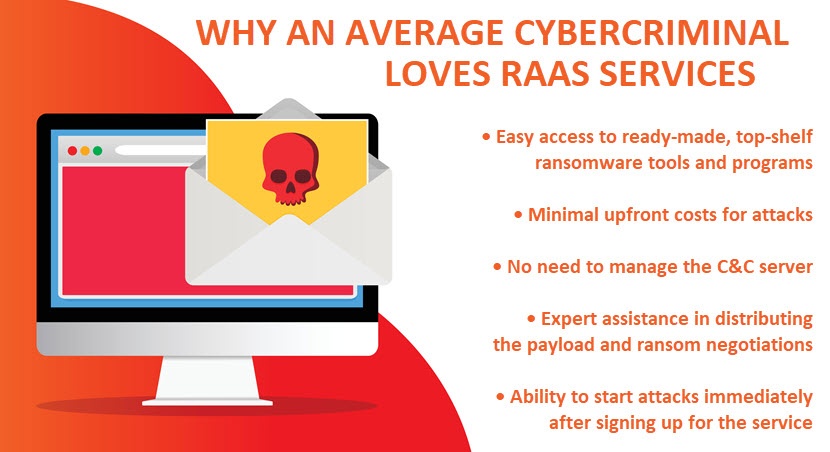
RaaS affiliates (attackers who distribute ransomware) get access to top-shelf software, which makes Ransomware as a Service ideal for criminals lacking the skill or time to create custom malware.Here’s what a typical RaaS kit offers:
- Ransomware software that encrypts specific files on the target’s system.Access to a command-and-control (C&C) server.
Detailed instructions on how to use the ransomware program and the C&C infrastructure.
- A payment processing system through which victims pay the ransom in cryptocurrencies.
- A dashboard that enables affiliates to track campaigns, monitor the number of infections, and view accumulated payments.
- Additional resources that help with ransomware delivery (e.g., data exfiltration tools, phishing email templates, exploit kits, malware-infected websites, etc. The majority of RaaS kits offer customization options, which allow affiliates to customize certain aspects of the software (e.g. ransom amounts, types of files targeted Some RaaS operators also provide benefits commonly offered by legitimate SaaS providers, such as:
- Dedicated 24/7 support.
- Detailed white papers.
- Playbooks and tip sheets.
- Training courses and videos.
Auto-patching.
- Access to affiliate forums and chat groups.
- Kits are easy to find on the dark web, where authors advertise RaaS packages as if promoting legitimate goods. The price of RaaS kits ranges from $40/month to a few thousand dollars (trivial amounts considering the average ransom demand in 2022 was $4.74 million).
- Experts predict that
- global ransomware costs will surpass $265 billion by 2031
- , and RaaS will play a key role in reaching that terrifying milestone. Check out our article on ransomware statistics for more must-know figures related to this cyber threat.
- Ransomware as a Service Examples
Although most RaaS programs are secretive by nature, some have gained enough notoriety to stick out from the crowd. Here are the most popular RaaS kits currently available to criminals (although arguably the most notorious RaaS of them all,
REvil is not on the list below since the group stopped operating in January 2022):Ryuk:
Ryuk has been available on a RaaS basis since 2019 and has “earned” over $150 million in ransoms. This group targets high-value targets, such as media outlets, government agencies and healthcare facilities. Affiliates are required to have some hacking skills in order to gain unauthorized access into target systems. Affiliates use manual hacking to gain unauthorized entry into target systems, so some skill is a prerequisite to becoming an affiliate.
RTM Locker: Read the Manual (RTM) Locker is based on the leaked source code from the Babuk ransomware. The gang behind RTM Locker runs RaaS campaigns in a corporate-like style in which affiliates must meet activity quotas and notify supervisors of their leaves.DarkSide:
- This RaaS program primarily targets Windows machines, although there have been recent reports of this strain targeting Linux devices. DarkSide is the variant responsible for the Colonial Pipeline attack in May 2021 that led to widespread fuel shortages across the East Coast.Dharma:
- Dharma first emerged in 2016, but the variant became available as RaaS in 2020. This strain is attributed by security experts to an Iranian threat organization, despite Dharma’s lack of central control. Dharma and its affiliates mainly rely on Remote Desktop Protocol (RDP) exploits.LockBit:
- LockBit is a RaaS kit available exclusively to Russian-speaking affiliates. LockBit, according to the author has been successful in targeting over 12,125 organisations. The malware is notorious for its ability to self-propagate and quickly exfiltrate files before encryption (that way, criminals get to further pressure victims with the threat of causing a data leakage).Our article on ransomware examples provides a comprehensive look at the different ransomware strains, families, and variants.
- How Does Ransomware as a Service Work?At the top of the Ransomware as a Service hierarchy are the operators who are responsible for:
- Developing the ransomware payload (either written from scratch or obtained from other hackers).Setting up and managing all back-end infrastructure required to run attacks (a C&C server, key management software, communication channels, and a payment processing system).
Creating a portal that enables affiliates to sign up and use the RaaS service.
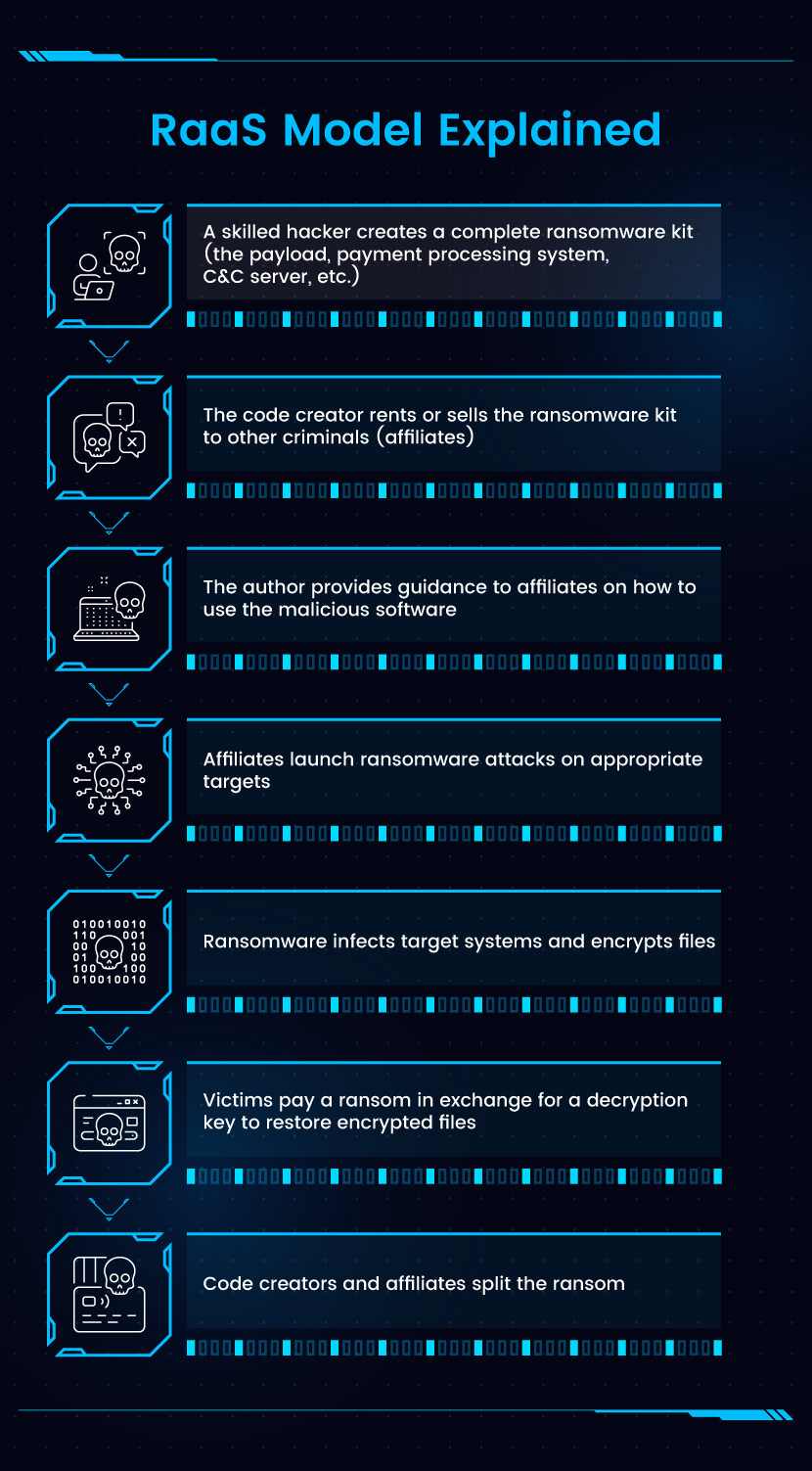
Preparing detailed guides on launching attacks with their software.
Once everything is ready to go, the operator recruits affiliates who lack the technical know-how or resources to develop ransomware on their own.
- Affiliates who get the “job” undergo extensive onboarding where the operator explains how best to infect target systems. Then, the affiliate gets a custom exploit code, as well as access to a portal for tracking:
- Infection statuses.
- Total made payments.
- The number of encrypted files.
General info about their targets.
RaaS affiliates also get access to various communities and documentation that help them better conduct attacks. The affiliate distributes payloads to victims using various attack vectors, including:
- Phishing emails with malicious URLs or attachments.
- Ready-made exploit kits.
- Drive-by downloads.
- Files with malicious Microsoft macros.
Social engineering is the go-to strategy since most RaaS affiliates lack the necessary know-how to find a zero-day exploit or set up a backdoor. In the event that an affiliate infects a computer, victims are instructed to pay a ransom for a key decryption. If the victim agrees to the demands, the affiliate uses the payment processing system set up by the operator to handle the transaction.
- Finally, the RaaS operator and affiliate share the ransom payment from the victim. The operator receives around 20-30% per ransom, while the affiliate gets the remainder. There are many different revenue models that RaaS operators use to make a profit. Here are the most common ones:
- Monthly subscriptions:
- The operator provides access to a RaaS service for a fixed subscription fee. Affiliates pay a monthly flat fee and get to use the software as much as they want for 30 days.
- One-time license fees:
In this model, the RaaS operator asks for a one-time fee in exchange for their software’s source code. Once an affiliate makes the payment, they gain indefinite access to the RaaS service.
Affiliate programs:
The RaaS operator asks for no upfront payments to use their software. Instead, the operator takes a predetermined percentage (usually in the 20% to 30% range) of every ransom payout.
Tiered systems:
Some RaaS operators use a tiered revenue-sharing system based on total ransom amounts or the number of successful infections. Revenue-sharing agreements are subject to negotiation between RaaS operators, affiliates and larger affiliates. Larger and more experienced affiliates typically enjoy more favorable terms, while newcomers to RaaS are often subject to below-standard rates.
- How to Prevent RaaS Attacks?Preventing RaaS attacks requires a proactive cybersecurity strategy that addresses the usual attack vectors. Here are the most effective precautions that reduce the risk of falling victim to a criminal using RaaS:
- Organize security awareness training to educate employees about the risks of ransomware and ensure everyone knows how to recognize suspicious emails, links, and attachments.Enforce the use of unique and strong passwords for all accounts, plus enable multi-factor authentication (MFA) whenever possible to add an extra layer of safety.
- Ensure everyone keeps their operating systems, applications, and anti-malware programs up to date with the latest patches.Make regular data backups of all critical files, plus use immutable backups to keep backed-up data safe from encryption attempts.
- Boost endpoint security to detect suspicious user behavior and isolate threats before they damage the network.Use zero trust security to limit user privileges and contain the impact of a potential infection.
Segment your network to separate critical systems from less sensitive ones and stop the spread of ransomware infections.
Deploy an intrusion detection system (IDS) to monitor network traffic for potential signs of ransomware activity.
Use Domain Name System (DNS) filtering to block communications between a would-be intruder and a C&C server.
- Disable macros in Microsoft Office and other productivity apps.
- Boost email security with message filtering and anti-phishing solutions.
- Use app whitelisting to reduce the risk of someone executing an unauthorized or malicious program.
- Run regular vulnerability assessments to identify and address potential weaknesses.
- Develop a disaster recovery plan that ensures your security team is ready to respond to a ransomware infection.
- Ensure your security strategy accounts for the latest ransomware trends, tactics, and indicators of compromise (IOCs).
- Ransomware as a Service Is Here to Stay
- The low technical barrier of entry and general ease of use required to pull off attacks will only make Ransomware as a Service more popular. Ransomware as a Service is Here to Stay
- The low technical barrier of entry and general ease of use required to pull off attacks will only make Ran
