It is time to rethink security and compliance. You can be compliant but not secure. In fact, you can be compliant but not secure.
Compliance doesn’t always achieve security.
Preparing For Todays Security Challenges
Information technology has grown in leaps and bounds over the last two decades with the industry set to top $5 trillion in 2019. This massive growth brings with it new security and compliance challenges. Insiders in the industry know it is increasingly important to control and understand how companies store, share and receive data. IT compliance frameworks are now in place to ensure this regulation of data happens securely, but they can differ extensively.
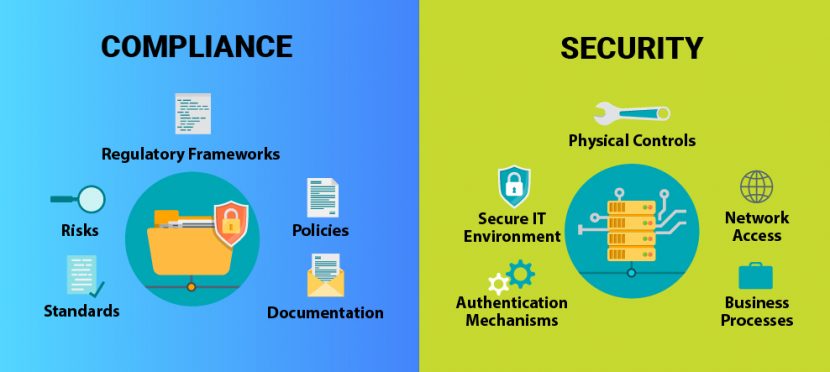
Breaking it down to its basics, becoming secure and compliant means securing information assets, preventing damage, protecting it, and detecting theft. Cybersecurity teams implement frameworks that are primarily technical in nature to achieve compliance. These are their main mandates and mantras. Compliance and security are not the same. To ensure proper protection, businesses must realize that Compliance is different from security. However, security is a big part of compliance.
What are the Differences Between Compliance and Security?
Compliance focuses on the kind of data handled and stored by a company and what regulatory requirements (frameworks) apply to its protection. It can be challenging for a company to understand the different frameworks that apply. They are primarily concerned with managing risk, which goes beyond the information assets. Compliance means that an organization is meeting the minimum security-related requirements. Compliance means ensuring an organization is complying to the minimum of the security-related requirements.
Security is a clear set of technical systems and tools and processes which are put in place to protect and defend the information and technology assets of an enterprise.
Compliance is not the primary concern or prerogative of a security team, despite being a critical business requirement. Security includes physical controls and who has access to the network. Security is easier to achieve than compliance because of the standard methods and tools that are provided by specialists. Compliance, on the other hand, can be multifaceted and is based on a company’s data type and security processes.
Compliance and Security Based on Specific FrameworksCompliance studies a company’s security processes. The compliance framework compares the security of a company at one point in time to a set of specific regulatory requirements. These requirements come in the form of legislation, industry regulations, or standards created from best practices.
Specifically, compliance frameworks include:
HIPAA
HIPAA (Health Insurance Portability and Accountability Act) applies to companies in the Health Insurance industry. The law regulates how businesses should secure and handle personal medical information of patients. HIPAA compliance is required by companies that manage such information. The act is divided into five Titles. Title 2 is the section that applies to information privacy and security.
Initially, HIPAA aimed to standardize how the health insurance industry processed and shared data. It has now added provisions to manage electronic breaches of this information as well.
SOX
The (also called SOX) applies to the corporate care and maintenance of financial data of public companies. The defines the data that must be retained and how long. SOX aims to increase corporate accountability and culpability. SOX requires all public companies to comply with its financial reporting requirements. Classifying data correctly, storing it safely, and finding it quickly are critical elements of its framework.
Sarbanes-Oxley Act PCI DSS
PCI DSS compliance is the Payment Card Industry Data Security Standard created by a group of companies who wanted to standardize how they guarded consumers’ financial information.
Requirements that are part of the standard are:
There are four levels of compliance within the standard. Levels of compliance are determined by the number of transactions that a business completes each year. Three different SOC reports exist. SOC 2 and SOC 1, which are two different types, cover personal information and compliance while SOC 2 covers financial information. SOC 3 Reports do not contain confidential information, as they are public. The ISO 27000 family is a set of standards that outlines the minimum requirements for securing data. As part of the International Organization for Standardization’s body of standards, it determines the way the industry develops Information Security Management Systems (ISMS).
Compliance comes in the form of a certificate. More than a dozen different standards make up the ISO 27000 family.
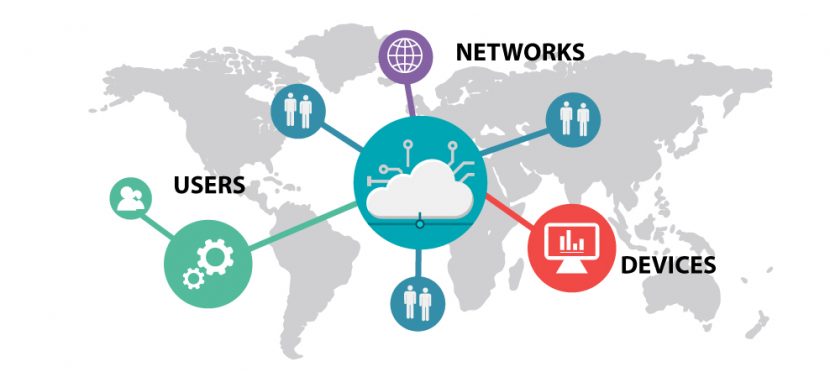
Security Covers Three Main Aspects of Your Business
1. Networks
Networks allow us to share information quickly over vast distances. They are also a security risk. A data breach can damage the image of a company. Loss or destruction of data can expose companies to criminal liability as they no longer comply with regulations. Protecting a network is one of the hardest tasks facing security professionals.
Network security tools prevent unauthorized access to the system. Data is protected by firewalls and software that filters content. Devices
A personal device connected to a network of a company can introduce unknown code. Similarly, clicking on the wrong email attachment can quickly spread malicious software.
2. Antivirus
Antivirus and endpoint scanning tools stop attackers from gaining access to the device. Phishing attacks and viruses have known signatures making them detectable and preventable.
Segmenting access to the network by device, user, and facility limits the spread of malicious software.
3. Users
Careless users are a significant risk for any company. They are unaware that they’ve been compromised or that they’re enabling an attack online. Phishing emails are now responsible for 91% of successful cyber-attacks.
Training users to be mindful can help limit innocuous yet dangerous actions. Training can increase security if employees know the risks involved in their daily use of technology.
Compliance and Security: The Perfect Alliance
Security is something all companies need. The majority of companies will have some level of protection in place when it comes IT infrastructure. This could even mean the bare minimum of having an antivirus installed on a workstation or using the basic Windows Firewall.
Turning security tools into a compliant IT system requires more effort. Company’s need to prove their compliance with the regulatory standards when a compliance audit happens.
Creating one system, an alliance of both security and compliance, in a systematic and controlled way is the first step in reducing risk. A security team will implement systemic controls in order to protect the information assets. A compliance team will then be able to validate that the controls are working as intended. This type of alliance will ensure that security controls won’t atrophy, and all the required documentation and reports are accessible for auditing.
Getting Started on a Secure Path
Compliance that meets a specific framework builds trust in a company. The added benefits of compliance are important, even though regulations will drive the process. Management should not rely on administrators to make important decisions about a company’s security. They must be able to understand all relevant information. Using compliance frameworks to find shortcomings in security is essential when looking at those decisions.
The road to compliance starts with:
Listing the current security tools used.
Conducting a risk assessment of the types of information processed.
Studying the requirements related to the framework.
Analyzing the gaps in your current controls in regards to the requirements.
Planning the way forward to solve major deficiencies.
Testing the efficiency of different solutions.
After applying these steps to a system, conducting regular assessments is the key to success. Compliance and security need to work hand in hand; it does not have to be security versus compliance.
They work in unison; how? Using a compliance framework, assessing security systems, correcting deficiencies, and then beginning assessments which are set on a regular schedule.
Security and Compliance: A Symbiotic Relationship
Security and compliance is a necessary component in every sector. Understanding how they relate to data security, is crucial. A failure in security can break a business.
Security and compliance are different components of a necessary and crucial system. Understanding how they relate to data protection can be crucial. Both are dependent on each other to maintain the highest level of data security. Compliance is not enough to ensure data security. The two must be in symbiotic relation. Now that you know the difference between security and compliance, read on to learn about the top security testing tools recommended for professionals. It’s time to take action against potential data threats and guard your cybersecurity.