This tactic is also highly effective–the FBI attributes more than $26 billion worth of losses to CEO fraud, making these attacks the most lucrative type of cybercrime. This tactic is also highly efficient–the FBI attributes more than $26 billion worth of losses to CEO fraud, which makes these attacks the highest-grossing type of cybercrime.
This article is a complete guide to CEO fraud that goes into all you need to know about this cyber threat.
What is CEO Fraud
CEO Fraud is a scam where a criminal impersonates an executive via email and tricks a lower-ranking worker into making an unauthorized wire payment. A CEO fraud email may not ask for direct money transfers. Instead, the scammer can order an employee to:
- Change the payment address of an existing invoice.
- Share the business’ bank or payroll information.
- Make gift card purchases.
- Disclose sensitive data that allows a criminal to blackmail or dig deeper into the company (such as client PII, tax statements, and company secrets).
- What Is CEO Fraud?
- CEO A criminal can also order an employee to:
- Change an existing invoice’s payment address.Share the business’ bank or payroll info.Make gift card purchases.
- Disclose sensitive data that enables a criminal to blackmail or dig deeper into the company (such as client PII, tax statements, or company secrets).
- CEO fraud caused
- $2.4 billion in losses to US businesses in 2021, equating to a third of the year’s total cybercrime costs. Here’s why these attacks are so effective:
The pandemic and the restrictions on in-person meetings caused an increase in email use, creating a fertile ground for CEO fraud.
The perceived difference in the hierarchy clouds the judgment of a lower-ranking employee. No one wants to upset or disappoint their boss, so people often do not second-guess requests coming from superiors.
If a scammer tricks a human, the criminal bypasses all cybersecurity best practices, tools, and policies the company has in place.
Compared to other types of cyberattacks, CEO fraud is relatively easy to pull off and (usually) does not require much IT skill.
- While the $26 billion figure is frightening, the actual all-time cost of CEO fraud is likely higher. Many attacks go unreported as organizations often decide not to report scams that cost them small amounts of money.
- Do not confuse CEO fraud with whaling, a phishing attack in which a scammer targets–rather than impersonates–a company executive.
How Does CEO Fraud Happen?
- Every CEO fraud starts with extensive research. The attacker gathers identity details for (at least) two individuals:
- The executive they plan to impersonate.
- The person they plan to target.
The attacker researches employees by:
- Scrapping info from the company’s official website, social media accounts, YouTube channel, etc.
- Gathering the info via social engineering tactics (e.g., pretending to be a salesperson over the phone and asking to speak to whoever’s in charge of budgeting).
- Visiting the office in person (e.g., acting as a courier or attending a job interview).
- The research phase sometimes lasts for weeks or even months while the scammer devises a plan. Criminals will approach their target by email and make a “fitting request” once they have identified a good opportunity. Some common tactics are:
Instructing the financial department to transfer money for a late invoice or fake merger.
- Asking HR to purchase gift cards and write them off as bonus expenses.
- Getting whoever’s in charge of wages to pay an invoice to a fake account, typically for an employee who allegedly did not receive the previous paycheck.
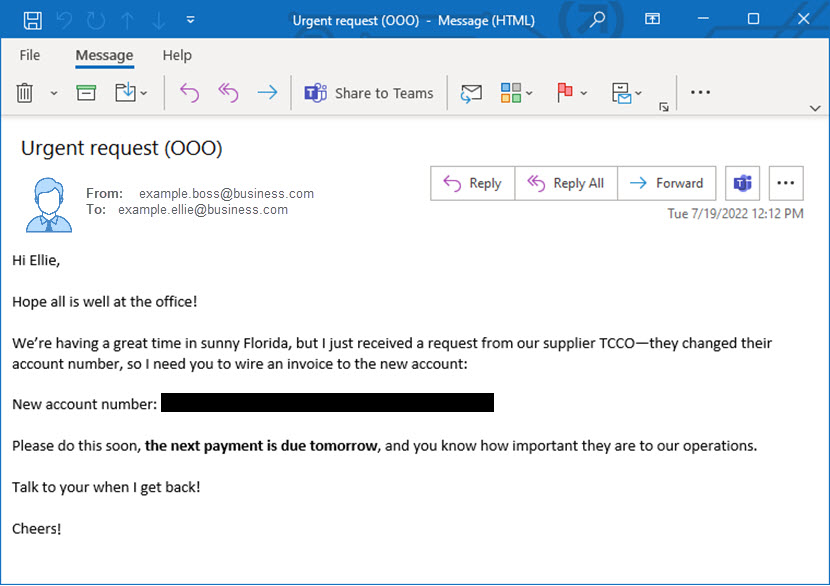
- Contacting an accountant as a supplier and claiming that they changed their bank account.Criminals use various tactics to fool employees, pretending to be executives, vendors, lawyers, etc. Most scams use urgency to pressure the recipient, like in this example:Scammers did their homework in this imaginary example:
- The executive probably is currently in Florida.
The “TCCO” might be a genuine supplier whose invoice is really due tomorrow.Fraudsters are using the sender’s unique writing style, picked up by scraping social media or analyzing previous emails on a hacked account.Attackers rely on various techniques to gather the necessary info and pull off CEO fraud. Let’s look at the most common ones.Domain SpoofingSpoofing an email means creating an email name almost identical to the address of the person you are trying to impersonate. Typically, the criminal alters the domain name slightly to mimic the corporate email (such as using “johndoe@betsbuy.com” instead of “johndoe@bestbuy.com“).
The goal is to create a lookalike domain that causes visual confusion. If the recipient is not careful, these little changes easily go unnoticed.
- Spoofed emails help an attacker perform research before launching a CEO fraud, but this technique also often enables a criminal to pull off the attack. Scammers will use a fake email if they cannot hack or access a legitimate email. This is a much more difficult approach. Read our article on email security best practices to learn what else you need to consider. Learn what else you must account for in our article on email security best practices.
- Phishing
- Scammers send phishing emails to employees to “fish out” sensitive info by posing as legit sources, such as:
- Banks.
- Credit card providers.
- Delivery firms.
- Colleagues.
- Law enforcement agencies.
The IRS.
Phishing helps a scammer to gather helpful intel for the upcoming CEO fraud. The phishing email may also contain malware which allows the criminal to hack into the account. The scammer then uses the address to either launch an attack or dig deeper into the organization.
- If the phishing campaign succeeds, an intruder gains access to company accounts, calendars, hierarchy, and other data that gives the details needed to carry out the scheme.
- Spear Phishing
Whereas regular phishing campaigns target multiple users, spear phishing goes after one specific employee. This calculated attack is used to trick the employee into revealing confidential information. The intruder then tricks employees by using the actual address, giving an apparent legitimacy to any request.
Email Account Compromise
Phishing is not the only method of hacking someone’s email account. Scammers who want to commit a CEO scam can also obtain email credentials by:
- Brute-forcing the password with a specialized tool.
- Luring users to fake login pages through their private social media accounts.
- Guessing easy-to-crack passwords.
- Purchasing previously cracked credentials on the dark web.
- Stealing BYOD devices from employees while they are not at work.
- Hiring more tech-savvy criminals that offer Business Email Compromise (BEC) services.
Once scammers get their hands on an email account, they start sending credible scam messages to employees. They also get access to all previous emails, enabling hackers to analyze how the manager communicates and imitate their tone of voice or incorporate commonly used catchphrases.
Our guide to strong passwords explains how to create credentials that are easy to remember and impossible to brute-force.

Who Is at Greatest Risk of Being the Target of CEO Fraud?
Cybersecurity studies suggest that almost 77% of CEO frauds involve employees outside financial or executive roles, so “building a wall” around staff members who authorize money transfers is not a sufficient defense.
Every employee is a potential victim of CEO fraud, either as the final target or a means to an end during attack setup. These employee groups are valuable targets because of their access to information or funds:
- Finance Department: Financial staff are the most likely candidates for CEO fraud. Criminals often target companies with sloppy policies that only demand an email from a senior position to initiate the transfer.
- Human resources: HR has access to every person in the organization and manages the employee database, so this department holds all the info necessary for successful CEO fraud. C-level executives are a key part of any CEO fraud scheme. They are the most common targets because they have financial authority in a company. If criminals steal the credentials of an IT manager, they gain entry to every part of the organization.
- Did you know that an average corporation experiences over 700 social engineering attacks every year? Learn how to protect your organization in our social engineering prevention article.Examples of CEO Fraud
- Let’s take a look at a few of the biggest CEO frauds to help you get a sense of how these scams happen:Toyota:
On August 14, 2019, a scammer convinced an employee at the accounting department of Toyota’s European subsidiary to transfer $37 million to a fake account. The criminal pretended to be a high-ranking executive and allegedly claimed that the company was not able to continue production without the funds.
- Pathe: France’s independent film group lost $22 million in an internet scam in March 2018. The criminals used the CEO’s personal email address to ask targets to send money to four accounts. Fraudsters stole $50m from Austria’s largest aerospace company, FACC AG. The crook targeted the financial and accounting department with a compromised CEO account.
- Crelan: In May 2016, Crelan Bank became a victim of scammers who used CEO fraud to trick employees into unlawful money transfers. The company did not reveal the exact strategy used to fool the target, but the bank reported over $70 million in losses.
- Puerto Rican government: Corporations are not the only victims of CEO fraud. Puerto Rico’s Industrial Development Company, which is responsible for the development of Puerto Rico, lost $2.6 million on January 17, 2020 in a phishing scheme. A crook posed as a beneficiary and asked the target to change a bank account tied to remittance payments.
- Once cybercriminals make their way into your system, CEO fraud is not the only thing to worry about. A data breach is another likely scenario, which is just as dangerous to your bottom line.CEO Fraud Prevention
- Below are the most effective methods for countering the threat of CEO fraud.Tips for companies
- Educate the staff about fraud tactics via regular training sessions.Require authorization for all transactions (plus double verification for any transfer over $5000).
- Create strict guidelines for changing payment details.

Prepare a disaster recovery plan to ensure you react quickly in case of successful CEO fraud.
Limit the info you share on official websites, job descriptions, and social media profiles.
Run periodic penetration testing to see how the team reacts to realistic scam simulations.
- Ensure employees use two-factor authentication on email accounts.
- Enforce strict, zero-trust security policies and review them regularly.
- Ensure everyone uses strong, unique passwords and that they update credentials every few weeks.
- Set up anti-malware tools, firewalls, intrusion detection systems (IDS), and email filters.
- Use protocols to control email activity (domain keys identified mail (DKIM) and sender policy framework (SPF)).
- Impose extra safeguards on high-risk users (C-level executives, HR, Accounting, and IT staff).
- Register as many domains as possible that are similar to your company’s domain.
- Tips for individual employees
- Verify every payment and purchase request in person.
- Check out the sender of every email by seeing their full address.
- Scan every email attachment with an anti-malware tool before you open anything.
- Contact the security team whenever something looks off or suspicious.
- Do not share info on social media that help scammers figure out passwords (e.g., pet names, birthdays, high school names, etc. ).
Know how to recognize phishing red flags in an email.
- Hover over every link to examine the URL before clicking.
- Never download anything from an email sent by an unknown party.
- How to Report CEO Fraud?
- Here’s a step-by-step instruction on what to do if you’ve been a victim of CEO fraud:
- 1. Contact your bank ASAP
- Inform the bank of the fraudulent wire transfer.
- Give them full details of the amount and where the money is going.
- Ask whether they can recall the transfer or intervene in some fashion (e.g., contact the bank on the receiving end and have them prevent the withdrawal or further transfers).
Contact attorneys
Reach out to your legal team and inform them of the incident.
Share all the facts related to the attack so that they start dealing with potential legal consequences.
- 3. Reach out to law enforcement
- Prepare a report for the officials with all relevant info (transaction details, date and time, email and IP addresses, accounts of previous phishing activity, etc. If you are in the US contact the local FBI office to report the incident. If you are in Europe, contact Europol. Otherwise, reach out to the local police department.
- 4. Brief your senior management
Call an emergency meeting of all executives.
- Brief the board on the incident, what steps you already took, and any planned further actions.
- Notify any third party that might face risk, such as a supplier or companies whose data you store.
Conduct IT forensics
- Have the security team investigate the breach and find the attack vector.
- Ensure the staff recovers control of all accounts and eliminates malware.
After addressing the immediate concern, create a plan to prevent the same incident from reoccurring.
- Unfortunately,
- companies recover less than 4% of fraudulently transferred funds
- . Consider taking out an insurance policy that covers you in case of CEO fraud (typically regarded as coverage for internal negligence or email impersonation, not as cyber security insurance)
Are Your Employees Ready for CEO Fraud Attempts?
- No one solution guarantees 100% protection against CEO fraud. To combat this threat, you must use a combination of technology, employee awareness and sound internal policies. A plan of action is also needed to prepare the team to respond to any scam attempts. You risk being caught off-guard, which can lead to CEO fraud.
