Should your business invest in Disaster Recovery (DR) or are backups sufficient to protect you? The methods and objectives of backups and disaster recoveries are similar, but they serve different purposes. Understanding the difference between a data backup and DR (and, more importantly, how the two work in tandem) is vital to creating a well-rounded, effective security strategy.
This article outlines the main differences between backups and disaster recoveries, two distinct practices that protect a business from data loss and unwanted downtime. We examine both concepts in detail, explain your options when deploying them, and show how companies use the two practices to avoid data and revenue losses.
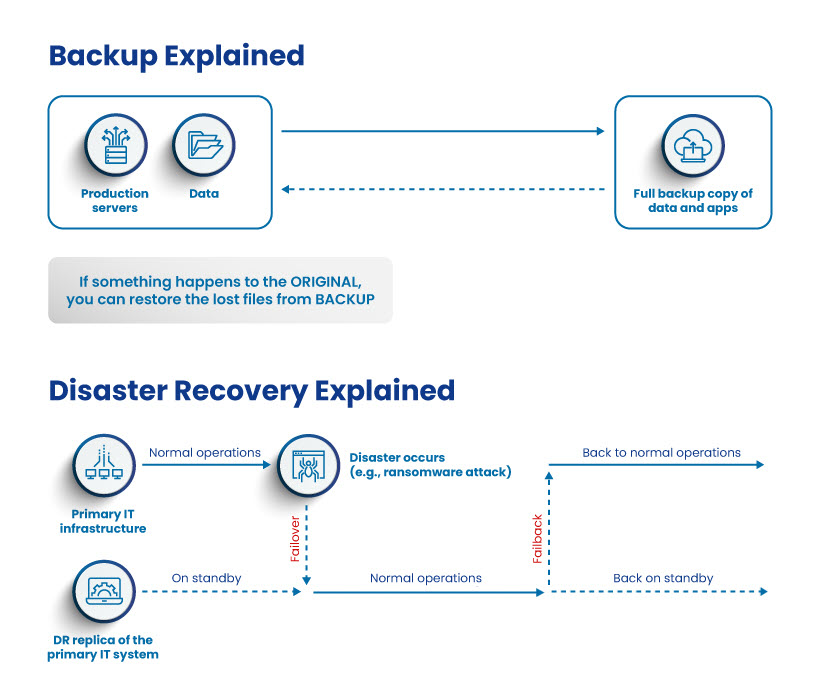
Backup vs Disaster Recovery
Both disaster recovery and data backups protect you in the event of failure, but these are two different practices:
Backup
- is an extra physical or virtual copy of data on another storage device (hard drive, CD/DVD, flash drive, cloud storage, etc.). If you lose a piece of data, you can use its backup to restore the original file.Disaster recovery (DR)
- is a step-by-step plan for responding to a major incident by switching to a secondary IT infrastructure. DR ensures critical functions keep running seamlessly during a natural or human-made disaster.While backing up data is integral to security, having backups is not the same as having a disaster recovery plan. Data copies are not enough to ensure business continuity if you experience a region-wide outage or large-scale cyberattack.
Backup vs Disaster Recovery (Table Comparison)
The backup vs disaster recovery table below offers a head-to-head comparison of the two practices:
Point of comparison
| Backup | Disaster recovery | Purpose |
|---|---|---|
| Provide a copy of valuable data in case something happens to the original file | Ensure the business can restore functions and avoid downtime during an unforeseen event | End-result |
| A copy of the original data | A functioning copy of the IT system on standby | Main countered risks |
| Host failures, small cyberattacks, accidental data deletion, and hardware failures | Region-wide failures (tornados, fires, power outage, etc.) and large-scale cyberattacks | Target devices |
| Servers, workstations, mobile devices | Critical servers, virtual apps | Scope |
| You back up individual files and VMs | A DR plan operates either on a per-department or business-wide level | Guarantee of business continuity |
| No guarantee | Aims to provide continuity in all scenarios | Mutual exclusivity |
| You can have backups without a broader DR plan (it will not be a sufficient defense, though) | Every DR plan includes some form of backup | Automation |
| Typically relies on a mix of automatic and manual processes | Usually as automated as possible | Average RTO |
| Speed is not decisive, so RTOs are typically long | Speed is paramount, so RTOs aim to be much shorter | Resource allocation |
| Backups usually sit in a compressed state and do not require much storage space | A DR plan requires a separate site with fully operational IT infrastructure (either hot, warm, or cold) | Complexity |
| All backup processes are relatively simple | Complex (setting up additional resources, prioritizing business apps, preparing for different scenarios, etc. ) | Data replication intervals |
| From time to time (hour, day, week, once per month, etc. ) | The replication of critical data happens continuously, ideally in real-time | Investment level |
| Even top-tier backups are highly affordable | Top DR plans require investing in a secondary IT infrastructure unless you go with DRaaS | What is a Backup? |
Backup is a physical or virtual copy of data that enables you to restore a file if something happens to the original. Data backups are essential to prevent data loss when:
Data theft occurs (office break-ins and data breaches, ransomware, stolen laptops etc.). ).
- Employee accidents (accidental file deletion, lost device, data leakage, etc. Technical issues (cracked hard drive, corrupted database, failed software upgrades, etc.). ).
- Natural disasters (fires, hurricanes, earthquakes, etc. Companies typically make data backups on a regular basis (every couple of hours, every day, weekly etc.). to ensure backups stay up to date. You can keep these “data save points” on various media and locations, both on-prem and in the cloud.
- Setting up the backup process is relatively simple as your security team needs to:
- Identify sensitive data.
- Choose a backup type.
- Decide how long you need to keep the backups and how often you need to back data up.
- Define the optimal backup interval.
- Identify incidents in which a company can lose data.
- Ensure backups comply with data storage requirements.
- Train the staff on the correct backup procedures.
- PhoenixNAP’s backup and restore offering presents a range of solutions you can use to ensure you retain valuable business data and maintain availability and business continuity even in case of a disaster.
- Types of Backups
- The table below presents the different types of data backup available to your company:
| Cons | Full backup | Copies the entire data set | A full copy of data set; simple to set up; highly reliable |
|---|---|---|---|
| Requires the most storage; uses a lot of network bandwidth | Differential backup | Backs up only the files that changed since the last full backup (e.g., if you have 50,000 lines of code and make changes to 50 of them, this backup type only affects those 50 changed lines) | Efficient use of storage capacity; quicker than full backups; faster restoration than an incremental backup |
| Uses more network bandwidth and space than incremental backups (still less than a full backup) | Incremental backup | Only updates the changes made to a file since the last incremental backup | Takes the least amount of space; fastest backup type; uses relatively little network bandwidth |
| Time-consuming restoration; complete restore is impossible if one of the incremental backups is missing | There is no reason not to use different backup types at the same time to improve resilience. You should follow | the 3-2-1 rule of backup | , a formula that stands for |
three copies of data on two types of media with one off-site copy. Off-site backup: A copy of data stored in a geographically different location than the original.Online backup: The use of a third-party service to back up data remotely over the Internet, typically on a cloud server. ).
- Off-site backup: A copy of data stored in a geographically different location than the original.
- Online backup: The use of a third-party service to back up data remotely over the Internet, typically on a cloud-based server.
- Snapshot vs Replication vs BackupData backups, replications, and snapshots are commonly confused, but the similarities between the three processes do not make them interchangeable:
A backup creates a replica of original data and enables you to restore files to a specific point in time, to one of the “save points” you take at periodic intervals.Replication means making copies of data while also synchronizing and distributing files among the company’s sites (servers, data centers, clouds, or hybrids). Data replication ensures that mission-critical applications continue to operate in the event of an incident.
A snapshot is a metadata-based record that saves the entire architectural instance of a virtual app, disk, or system. These “photos”, which are metadata-based records, allow you to restore virtual machines and servers in the event that data is lost or corrupted. Snapshots are not data copies, so they do not take up much space (but their total volume can grow, so always place a cap on the number of stored snapshots).
Backups, snapshots, and data replicas are not mutually exclusive, so you can use all three to keep your data safe. However, you should know the difference between these practices to create an effective data recovery strategy.What is Disaster Recovery?
Disaster recovery (DR) is a set of policies and procedures that enable a company to quickly regain the use of IT systems during a natural or human-made disaster. DR, on the other hand, is a strategy that ensures business continuity under different scenarios. These can include situations where critical operations are disrupted (or stopped completely). Here are some examples of unforeseen events:
Cyberattacks (malware, DDoS, ransomware, APT attacks, etc. Here are some examples of unforeseen events:
Cyberattacks (malware, DDoS, ransomware attacks, APT attacks etc.).
- Sabotage(both from an outside and insider threat).
- Power outages.
- Equipment failure.
- A terrorist attack.
- Loss of valuable data.
- Natural disasters (hurricane or tornado, flood, earthquake, etc.). A disaster recovery plan includes the ability to switch to redundant servers and storage systems. There are three types of backup facilities based on how quickly you can get a site up and running:
- Hot site that contains all the necessary equipment, tech, and current data.
- Warm site equipped with the necessary equipment and tech but without updated data.,
- Cold Site that only hosts the IT infrastructure.
- High recovery costs.Supply chain disruptions.
- Hits to employee satisfaction. There are three types of backup facilities based on how fast you can get a site going:
- Hot site that contains all the needed equipment, tech, and up-to-date data.
- Warm site equipped with the necessary equipment and tech but without up-to-date data.
- Cold site that only hosts the IT infrastructure.
- Not having a DR plan in times of disaster can negatively impact an organization and lead to:
- Interrupted service.
- Permanent data loss.
- Lost sales and revenue.
- High recovery costs.
- Supply chain disruptions.
- Hits to employee and customer satisfaction.
- Loss of reputation.
Puyka’s disaster recovery offers top-tier yet affordable DR solutions that provide all you need to create an effective disaster recovery plan.
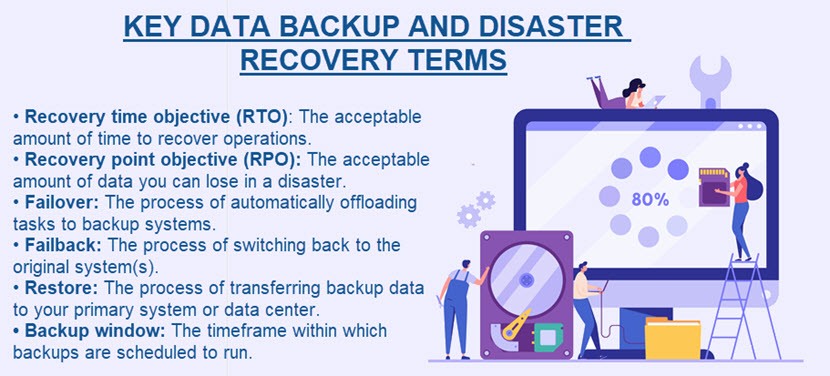
- RTO vs RPO
- Recovery time objective (RTO) and recovery point objective (RPO) are two critical metrics in disaster recovery. These metrics are:
- RTO represents the maximum amount of time before a system can be brought back online. RTO is the maximum amount of time that can elapse before a system must be brought back online. For example, voice control systems in a business can have a RTO of 10 minutes. This means the system has to come back online within ten minute of being down. If a database’s RPO is four hours, then the system should be backed up every four hours. RTOs are determined by a company based on the amount of time it can tolerate for a system not to be available in case of disaster. RPOs also vary as each business must estimate its:
- Industry-specific factors (such as fines for losing financial transactions or health records).
- How data storage types affect the speed of recovery.
The cost of data loss.
Data availability needs.
RPOs also vary as each business must estimate its:
- Industry-specific factors (such as fines for losing financial transactions or health records).
- How data storage types affect the speed of recovery.
- Maximum tolerable data loss.
- The cost of data loss.
- Data availability needs.
- While disaster recovery (DR) and business continuity (BC) have similar goals, these are two separate strategies. Get a head-to-head comparison (as well as valuable tips for both) in our business continuity vs disaster recovery article.
- Disaster Recovery Plan
- A disaster recovery plan is a formal, business-wide document that outlines the company’s approach to dealing with an unfortunate event. A DR plan should include:
- A DR policy statement and plan overview.
- All recovery goals (including RTOs and RPOs).
- A step-by-step guide to disaster response actions for each incident type.
Sketches and diagrams of the entire network and recovery site.
- A list of all staff members responsible for DR.Contacts of go-to DR team members.
- An asset map.A list of systems needed for disaster recovery.
- Technical documents.Directions for reaching and activating the recovery site.
- Actions for dealing with legal issues.Each business has a unique disaster recovery plan, but there are some common traits in every strategy. Here are some general tips.
- Risk assessments: Begin building your strategy with a business impact analysis and risk evaluation. This step will help you identify the threats that are most likely to affect your business. Assets should be ranked according to how likely they are to disrupt business operations if they were to go down. Order assets by how likely they are to disrupt business operations if they were to go down.
Create a dedicated disaster recovery team:
The DR team is an assigned group of staff members responsible for designing and implementing the disaster recovery plan.
Test your DR procedures:
Regular tests ensure the plan stays efficient and that the staff knows how to act in case of an incident.
- Keep updating your DR plan:
- A disaster recovery plan should be a living document that evolves alongside your organization. Adapt the strategy whenever you add new devices, expand infrastructure, or discover better backup options.
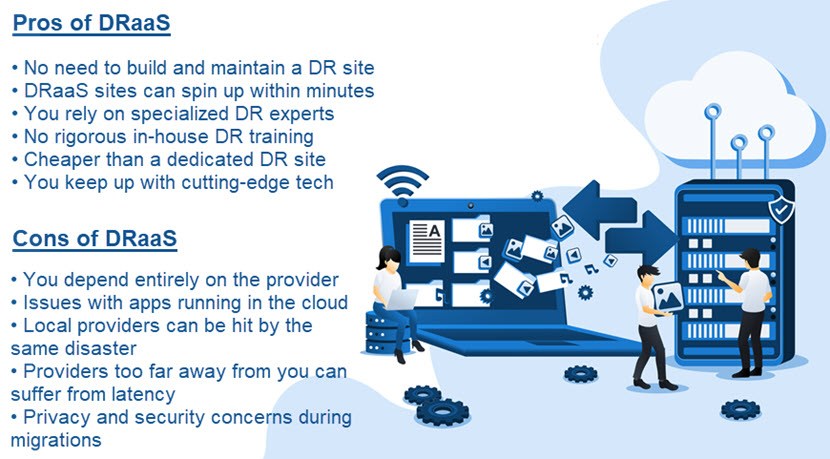
- Disaster-Recovery-as-a-Service (DRaaS)
- Disaster-Recovery-as-a-Service (DRaaS) is a managed approach to DR in which you outsource a third-party provider to host and manage the backup infrastructure. DRaaS offers a great alternative to a dedicated DR solution as it eliminates the need for a standby environment and the associated costs. Let’s look at a real-life example of what DRaaS offers. Let us say that you run an e-commerce business and that a ransomware attacker targets your website:
- Your staff starts reporting that the website is acting up when you realize someone used encryption to scramble several databases.
You declare a disaster, reach out to your provider, and instigate a DRaaS failover.
The provider moves your system to its cloud infrastructure in minutes, allowing you to continue operations from a preset environment.
Your in-house team searches for the source of the attack and eliminates the threat. Meanwhile, the website operates without issues, and end-users are unaware of what is going on behind the scenes.
