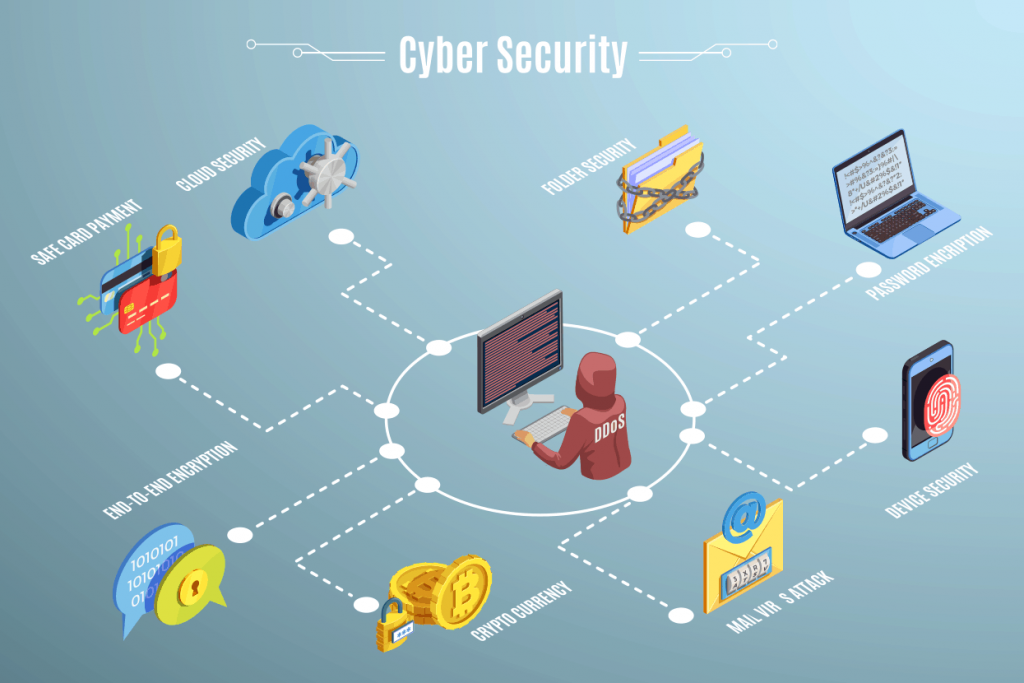
Cybersecurity is high on the list of concerns for rapidly evolving businesses online. As more small businesses move services or store data online, they are putting themselves at risk for cyberattacks.
At the forefront of this battle against cybercrime and hackers, companies must consolidate a solid defense by implementing cybersecurity best practices. This article will cover key strategies every company should adopt to avoid attacks and become less exposed.
Cyberattacks aim to compromise systems and access relevant data that they can monetize, ranging from stolen credit card information or credentials for identity theft.
Strong cybersecurity policies and procedures can save millions of dollars for organizations. The initial investment is required to create a secure network and prevent intrusions. Cyberattacks are becoming more severe and widespread every day, and they pose a serious threat. Thus, the need for safeguarding against such dangers is critical.
Recommended Cybersecurity Best Practices
Adopt the cybersecurity best practices below to prepare your organization against cyber threats and ensure the continuity of your business.
1. Create an Insider Threat role
An interior threat program is a key part of modern cybersecurity strategies. Employees who have access data can cause leakage of information or even damage equipment. It is important for companies with sensitive data to create an insider-threat program. They could lose their reputation if they are exposed by an insider. It does come with a cost and can be considered a low priority task, businesses should not delay, and instead, gain the support of top management to develop policy across all departments.
2. Conduct Phishing Simulations
As of 2020, phishing attacks are one of the most prevalent forms of cyber threats experienced by companies on a global level. Employees should be trained on how to avoid downloading files or clicking on malicious links through phishing simulations. By raising cybersecurity awareness through simulated phishing, employees can better understand the effects of a phishing scam. The simulation provides a safe environment for employees to test their knowledge, ask questions and learn the latest tricks.
3. Secure Remotely Working and Travelling Employees
Many corporate employees have the dangerous habit of accessing corporate networks through unsecured public Wi-Fi networks while traveling on work trips. Employees should understand that sacrificing security for convenience in the corporate world is unacceptable. It is important to educate and train employees on how to minimize risks. Using VPNs when surfing the internet while traveling and installing anti-malware software will help tighten security gaps for your employees outside of the office. Read our article about remote access security.
4. Prioritize employee privacy
Data Privacy Awareness and Digital Data Sensitivity Concerns are at a record high. New legislation is being introduced to better regulate them. By “anonymizing”, employee privacy can be prioritised. Create a Cybersecurity Awareness Training Program
5. Create a Cybersecurity Awareness Training Program
Company surveys have found that two out of three insider threat incidents are initiated by an employee or contractor, which can be prevented (ObserveIT). The first line of defense in the fight against cybercrime is your employees. Education is essential to develop the skills and knowledge required to protect an organisation. A comprehensive cybersecurity awareness program will create a critical “security-first culture.” It would address aspects such as identifying risks, changing employee behaviors, and tracking metrics of improvement.
6. Inform Third-Party Contractors of Cybersecurity Policy
Globalization and interconnectivity have led many businesses to assign specialized tasks to third-party contractors or external entities. These third-party contractors must be informed of your cybersecurity policies. The cybersecurity policies must be communicated to both internal staff and third-party contractors. Implement
7. IS Governance Approach
Every company should establish and maintain an information security (IS) framework that aligns with the business’s existing assurance strategies. It is important to ensure that all management levels can use a risk-based strategy when selecting one of these programs. This strategy allows staff to detect incidents faster, investigate them and respond more quickly.
8. Monitor User and File Activity
Malicious insider threats tend to take advantage of multiple channels to exfiltrate data. One of the best ways to solve this problem is by developing a system that monitors user and file activities. Data loss prevention solutions, which only focus on data, and not user activity, do not prevent malicious insider threats. It’s much easier to prevent or react to a security incident if you closely monitor your users and know which files they are accessing. Be aware of state-sponsored threats.
It has been well documented that employees in high-value industries like healthcare, banking, technology and banking are susceptible to financial incentives to sell their data to foreign governments or entities. Understanding the motivations of these entities and possible insider targets will help you spot patterns of suspicious or underhanded behavior. Enforce Password Managers and SSOs. The best way to address potential security weaknesses in your organization is by implementing an enterprise password solution.
9. Audit Privileged access
The head management of a company should review the number users with privileged access. It is necessary to grant privileged access, particularly when staff changes or roles are changed. Businesses should regularly look at permissions, adopt a system of temporary or rotating credentials, or develop a system of auditing privileged accesses.
10. Essential Network Security Practices
Security teams are held accountable for addressing the risk of insider breaches. Take a systematic approach to organizing security measures when developing a plan against insider risks. Here are some essential network security practices:
11. Stop Data Loss
Enterprises regularly experience the problems caused by leaked and stolen data. Data exfiltration is a major security concern for modern businesses. To get a full picture of the way all parties handle and access data, companies should control access, monitor vendors and contractors, and also employees. Detect Insider threat
While trained users are the first line of defense for a company, technology is still its main tool. Regularly monitoring user behavior can help companies detect unauthorised behavior.
12. Back-Up Data
Backing up data regularly should be a mandatory practice, especially when you consider the malicious ransomware out there like “Wannacry” and “Petya.” Back-Up Data
Backing up data regularly should be mandatory practice, especially when you consider the malicious ransomware out there like “Wannacry” and “Petya.” Data back-ups are good practice to include in one’s basic security hygiene, as well as to combat emerging cyber threats.
13. Beware of Social Engineering
Social engineering tactics are considered a threat and have been used for decades to gain login credentials and access to files that are encrypted. These attempts can come from phones, emails, profiles on social media, etc. In such circumstances, the best defense is to do the following:
14. Outline Clear Use Policies for New Hires and Third Parties
Requirements and expectations that the company has, regarding IT security, should be clearly stated in the employment contracts and the various SLAs and SOPs that a company might have.
15. Update Software and Systems
Cyber crimes and threats are increasing, and a security network that is optimized for protection may fall victim to them. A company’s network must be always protected. Plan regular software upgrades and schedule hardware security maintenance.
16. Create a Playbook for Incident Response
Nothing can stop cybercrime, no matter what security measures are taken. Companies should prepare a security incident response plan in the event they are attacked. This planning will allow management to limit the damage of a security breach, allowing them to remediate the situation effectively.
17. Educate and Train Users
Employees should be trained on how to create and maintain strong passwords, recognize phishing emails, avoid dangerous applications, etc. Maintain Compliance
No matter what level of cybersecurity a company implements or already has, it should always comply with regulatory bodies such as HIPAA, PCI and ISO. Maintain Compliance
No matter what level of cybersecurity a company implements or already has, it should always comply with regulatory bodies such as; HIPAA, PCI, ISO, and DSS and keep up with their latest guidelines.
18. Additional Practices to Improve Cybersecurity
Build Processes before Choosing Tools: Organizers should implement a formal security governance program and think through the strategies that they will implement before deciding on tools, equipment, or software.
Recruit HR to Halt Data Loss: Companies should recruit HR teams that can develop and execute better off-boarding processes to protect data. They can do this by systematically removing accesses from employees who have left or are on the verge of leaving.
Prioritize Visibility: Insider threats that are malicious and accidental can be prevented by continuously monitoring user activity. Thus, the software chosen should also give management, unfettered visibility.
- Automation: Small things such as system updates should never depend on user discretion. Whenever possible, automatic updates, incident detection, etc. Automated systems can reduce the risk of human error. Only complex and strategic actions and other activities requiring human intervention can rely on employees.
- Compliance with GDPR: The General Data Protection Regulation (GDPR) is the regulatory body responsible for regulating data privacy for all European citizens. The majority of companies that operate within the European Union must comply with this directive. Google also encourages companies to use HTTPs in order to provide secure and private connections for their users’ connection to their websites. This extra level of security is one of the first steps in implementing the essential methods of site encryption, data integrity, and authentication.