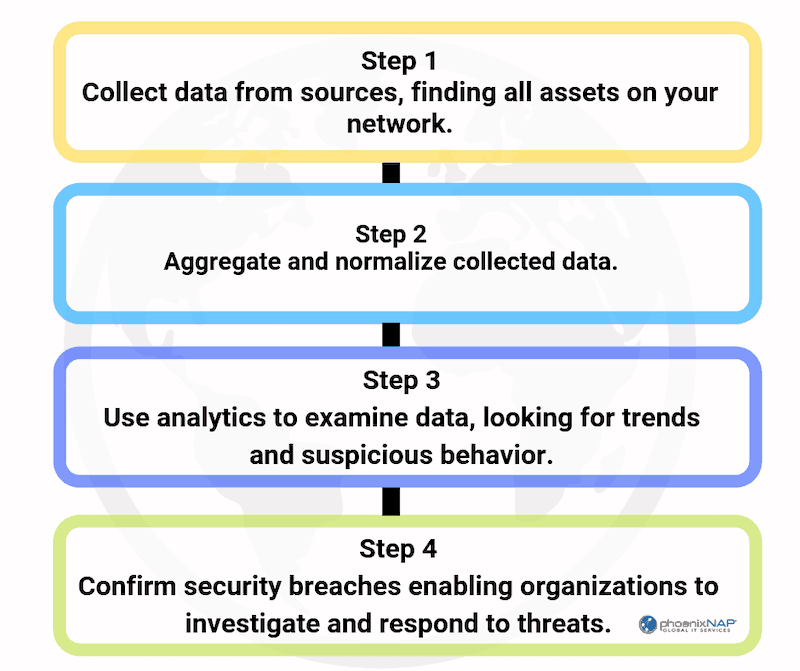
Choosing the right Security Information and Event Management software can be overwhelming.
The SIEM market today is nearly a $3 billion industry and growing. As you evaluate threat detection systems, identify the tools that you will need to protect your company against different types of cyberattacks. Examine how you should build out your protection.
Take the time to consider the preparations necessary for successful expansion into the technology. The benefits of a sound, real-time security system are well worth the investment.
What is SIEM?
SIEM or Security information and event management is a set of tools that combines SEM (security event management) and SIM (security information management) Both of these systems are essential and are very closely related to each other.
SIM refers to the way that a company collects data. SIM is the way that a company collects data. This format is then stored in a central location. SIM is not a comprehensive enterprise security solution. It’s often misunderstood as such. SEM monitors systems in real time and alerts network administrators to potential problems. It can also establish correlations among security events. The software sends log data to a central portal. Cloud servers are usually used, as they offer a more robust level of security monitoring. A console allows clients to filter visual aids by local parameters. Accounting logs can be used to identify, recreate, and audit cybersecurity incidents. Advanced platforms include entity and behavior analysis (UEBA). SOAR may be included in other systems. SOAR stands for “Security Orchestration and Automated Response.” UEBA and SOAR are very helpful in specific instances.
Security Information and Event Management also works by monitoring and logging data. Most security operations experts consider SIEM tools to be more than a simple monitoring and logging solution.
A SIEM security system includes:Actively develops lists of global threats based on intelligence.
Collecting logs from vetted sources of intelligence.
A SIEM solution consolidates and analyzes log file, including supplemental analytics data to enrich the logs.
Finds security correlations in your logs and investigates them.If a SIEM rule is triggered, the system automatically notifies personnel.
Best Practices for Using a SIEM Solution
Identify Critical Assets To Secure
- The first thing organizations must do is identify critical assets thru security risk management. The first step in implementing a SIEM solution is to identify critical assets. Prioritizing assets allows an organization to maximize its security within a budget. Prioritizing assets allows an organization to maximize its security within a budget.
- Prioritizing assets also help in selecting a SIEM solution
- Understanding a companies needs also helps to scale the SIEM platform used. SIEM technology can help with low-level compliance efforts without much customization.
- Enterprise visibility is another goal altogether. This goal requires a higher level of deployment. This goal doesn’t require as much customisation. Take the time to develop a detailed strategy before investing. Take the time to form a detailed strategy before investing.Train Staff to Understand SIEM SoftwareThe second step is to ensure that in-house staff understands SIEM as a platform.
- What system log files will the SIEM technology solution monitor? What system log files will the SIEM technology solution monitor? Data may be processed differently by different departments. Before a SIEM can help you, these logs must be normalized. The system cannot perform at its full potential or produce actionable reports with different logs. Why? The data is not consistent.
Create a Scaling Strategy
Some companies duplicate a logging strategy as they expand. The number of servers required will increase. The company will reproduce the log rules as it grows. As time passes, the log files will replicate themselves. This helps preserve records if a company is acquired or merges with another.
Creating a viable strategy becomes more difficult if servers are spread throughout different time zones and locations. Ideal would be to standardize your organization’s time zone. Neglecting this step may lead to unsynchronized time stamps. Make sure the SIEM solution meets your needs. Syslog logs, for example, connect via outsourced agents. Microsoft logs deal with agents that are locally installed. The logs are collected centrally using a Remote Procedural Call or Windows Management Instrumentation. Only then are they given to the devices collecting logs.
Executives are responsible for determining the security needs of each prioritized asset. This is essential to produce measurable and actionable results from a SIEM.
Log Only Critical Assets (at First)
Secondary features can roll out after configuring the full log environment. This helps avoid mistakes by managing this step-by-step. The capabilities of the
SIEM products are different. Make sure that you vet each system based on your individual needs.
OSSEC
Open source SIEM is quite popular.
has been used most commonly as a host based system for intrusion detection and prevention. This system is sometimes abbreviated IDS. OSSEC supports Solaris, Mac OS and Windows Servers, as well as Linux and Linux. The structure of the program makes it work well. Two components comprise OSSEC: 1. the host agent and 2. the main applications.
OSSEC allows direct monitoring for rootkit detection, file integrity, and log files. It can connect to IDS platforms based on FTP, DNS, DNS, mail, firewalls, and web. You also can synchronize log analysis from primary commercial network services.
Snort
is a network-based IDS. It is located further away from the host and can scan more traffic. Snort is one of the best SIEM tools. It analyzes network flows in real time. The display of Snort is robust. You can display packets live, analyze packets or dump them. It is a complex system to configure, but it’s worth it. Snort is a powerful tool, so make sure your staff knows how to use it. This SIEM tool has a wide range of uses. You can use this SIEM tool in many ways.
ELK
may be the most popular solution in the market. The ELK stack is the combination of products from SIEM vendors Elasticsearch, Logstash, and Kibana.
Elasticsearch provides the engine to store data. It is considered a top solution in the marketplace.

Logstash can receive your log data from anywhere. It can also enhance, process, and filter your log data if needed.
Finally, Kibana gives you your visuals. Kibana is a powerful tool that has no equal in the IT world. This stack is the foundation of many commercial Security Information and Event Management Platforms. The stack is more stable because each program has a specific purpose. This is an excellent choice for high performance and a relatively simple learning curve. PreludeAre you making use of various open-source tools?
Prelude gives you the ability to store logs from multiple sources in one place. This is done using IDMEF (Intrusion Detection Message Exchange format). You can analyze, filter, correlate and alert your data. Commercial version is better than open-source. If you need top performance, go commercial. OSSEC OSSIM SIEM Solution ELK is one of the top SIEM solutions.
comes in second. OSSIM, the open-source version of Alien Vault’s Unified Security Management Package, is a close second. It uses an automated testing framework similar to Prelude. It is regarded as an excellent tool.
SnortOSSIM, as a commercial product, is more robust. Open-source SIEM works well for micro deployments. Get the commercial offering if you need performance at scale.
SolarWinds SIEM Log Manager
You get the event log analyzer and management consolidator for free as a trial. You can view logs from multiple Windows systems with SIEM systems. You can filter logs. The Security Events Manager gives you the capacity to assess and store your historical log data.
ELKSolarWinds is one of the
most competitive entry-level SIEM security tools on the market
. The dashboard is a nice touch. It is detailed and intuitive. The user can quickly identify any anomalies because of the attractive and easy to use display.
The company offers 24/7 support as a welcome incentive, so you can contact them for advice if you have issues.
LogFusion SIEM Software is a simple program. The program has a flat learning curve and a simple interface. This platform is for you if you need to manage remote logging, event channels, and log dumps from a single interface. This allows you to consolidate events from across a network into a single place. You can send email alerts instantly. You also have a limited ability to archive and some alert criteria filtering for extra measure.
McAfee Enterprise Security Manager SIEMPrelude is one of the best options for analytics. McAfee’s correlation engine allows for efficient and effective normalization of disparate data sources. This ensures that it’s easier to detect when a security event needs attention.
With this package, users have access to both McAfee Enterprise Technical Support and McAfee Business Technical Support. The user can choose to have their site visited by a Support Account Manager twice a year if they would like, and this is recommended to make the most of the services.
This choice is Best for mid to large companies looking for a complete security event management solution.
RSA NetWitnessOSSIM offers a complete network analytics solution. For larger organizations, this is one of the most extensive tools available.
However, if you’re looking for something simple, this is not it. It is difficult to set up and use the tool. Although comprehensive user documentation can assist you when setting up, the guides don’t help with everything.
LogRhythm Security Intelligence Platform
LogRhythm can help in numerous ways, from behavioral analysis to log correlation and even artificial intelligence. The system can be used with a wide range of logs and devices. You can, for example, use the Windows Host Wizard in order to look through Windows logs. The manual provides hyperlinks to features so you can find the links that will help. The manual has links to the features, so you can easily find them.SolarWindsSplunk enterprise security
may be the most popular SIEM solution in the entire world. Display alerts can be defined by you. Display alerts can be defined by you.The user interface is incredibly simple when it comes to responding to threats, and the asset Investigator does an excellent job of flagging malicious actions.Papertrail by SolarWinds SIEM Log Management
is a cloud-based log management tool that works with any operating system.
Papertrail has SIEM capabilities because the interface for the tool includes record filtering and sorting capabilities, and these things, in turn, allow you to perform data analysis.
Data transfers, storage, and access are all guarded with encryption. Only authorized users are allowed access to your company’s data stored on the server, and setting up unlimited user accounts is simple.
Performance and anomaly alerts are provided and can be set up via the dashboard and are based on the detection and intrusion signatures stored in the Papertrail threat database.
LogFusionPapertrail will also store your log data, making them available for analysis.
Logstash
is one of Netwrix Event Log Managerthree software solutions that work together to create a full SIEM system. The user can use each application with other tools according to their preferences. It is not mandatory to use all of them together. All of the modules are open source and free for the user.
McAfee Enterprise Security ManagerLogstash collects log data from the network and writes them to file. You can specify in the settings of Logstash which types of records it should manage, so you can ignore specific sources if you wish.
The system has its own record format, and the Logstash file interface can reinterpret the data into other forms for delivery.
SIEM Tools and Technology: Key Takeaways
Cybersecurity tools and threat detection are a must to secure data and prevent downtime. Vulnerable systems are always a target of hackers, and this is why Security Information and Event Management products have become a crucial aspect in identifying and dealing with cyber attacks.
The RSA NetWitnesstop SIEM products provide real-time analysis of security alerts and are essential to identify cyber-attacks.